Monday, May 23, 2016
HOW TO REMOVE LOCKY VIRUS
This page aims to help you remove Locky Virus Ransomware. These Locky
Ransomware removal instructions work for all versions of Windows. We
were recently asked in our reader’s comments about how to restore “locky
datei” and we feel we should help users understand how to do it. To
restore “locky datei” you will likely have to revert back to a previous
date before the ransomware infected your PC. But, it may be very hard to
do so, as the virus will undoubtedly try to hinder your process and may
even succeed. This ransomware uses a different encryption method from
most of its other peers – the AES-128 military grade encryption. The
Aes-128 encryption is a step up for the creators of crime software, as
it has previously not been exploited in such a way. Considering that the
targets of this scam are predominantly German citizens, it is likely
you will have your hands quite full. The
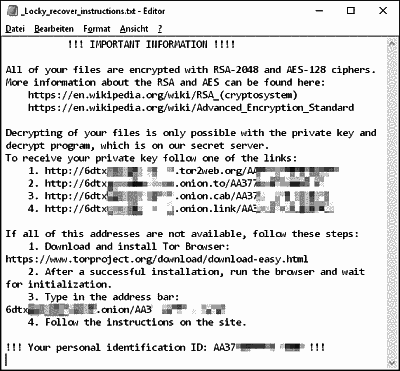
_Locky_recover_instructions.txt ransom note is practically identical to a
lot of others out there, so this is a general shoutout: DO NOT PAY UP!

locky virus removal
There are several reasons for this, the most notable of which are:
- If you pay, you will have to login with accounts that may already be exposed. If they are not already stolen however, you basically risk showing them to people who are already monitoring you via a Trojan.
- By paying up you may or may not recover your files – but every time someone pays the ransom, the criminals grow stronger. They develop their software even more and people like you suffer
- There is really no reason for them not to give you your files back – but at the same time, there is always the chance you will pay but the files are not released and you will continue to search for a “locky datei” solution.
If
your files have already been encrypted by Locky Virus, then you are in
some serious trouble. Don’t panic though – we’ll try our best to help
you with this article. What you are facing is a very dangerous virus of
the ransomware type. These viruses have gained a lot of notoriety,
because they encrypt your files and make them unusable, but the process
is not reversed if you delete the virus. This gives the hackers a lot of
leverage that they will undoubtedly use to blackmail you for a ransom,
if they haven’t already. You will need to learn some more basic info on
ransomware viruses before you can deal with fichier locky effectively,
so please keep reading. This will also shed a light how to perform
a “locky datei” recovery and how to avoid getting a locky recover
instructions ransom note.
Locky Virus – first stage
When
your computer was first infected with the ransomware it began
encrypting your files. Depending on the size of your HDD and how much
data you had the process could have taken a couple of hours or even
days. The virus remains out of sight during this, but you may have
spotted signs of its presence – your PC performing poorly than usual,
programs taking ages to load. Encryption is a memory and CPU intensive
process and takes a toll on your system resources – in the future if
your computer is working poorly open the task managed and look at what’s
eating the resources. Ransomware viruses usually try to pose as windows
programs and services, so if you see two of those with the same name
and one of them is taking a lot of CPU power you’ll have your culprit –
immediately shut down the process and delete all associated files or
better yet pull the plug on your PC and find an expert.
Locky Virus – reveal
If
your files have already been encrypted, then you have probably already
seen the ransomnote generated by the virus. It probably has some kind of
timer to put pressure on you and it demands the payment to be made in
BitCoins. The criminals are now hoping that the surprise shock will put
you to the edge and you’ll pay them the ransom. Well… that’s really not a
good idea, for a couple of reasons.
- Paying money to cyber criminals only encourages them to get better at their craft and extort even more people.
- You are not guaranteed in any way that your files will be decrypted successfully if you make the payment.
- There is absolutely no reason to pay until you’ve tried all the free methods first.
The
methods we’ve provided at our guide do not provide guaranteed recovery
of all files, but they are an excellent start. Paying the ransom should
only ever be considered if all other options are exhausted and the
documents encrypted are worth much more than the ransom money.
There is a good chance you have a Trojan horse in your computer
While
it is certainly possible that you unknowingly installed Locky Virus on
your own computer chances are that a Trojan horse actually did it.
Trojan horse viruses are the preferred method of spreading ransomware –
they are very subtle and not all anti-malware programs can detect them
and they can remain on an infected computer for a really long time.
Trojan horse viruses that deliver ransomware are also known as
“droppers” and you should make sure that you don’t have one of these
installed on your computer. It can always download new ransomware if
left alone. Unfortunately, such a search is next to impossible to
perform manually – you’ll have to trust an anti-virus or an-anti malware
program with it. If you don’t have one or if the one you have failed
you with the ransomware feel free to check out our recommendation by
clicking on one of the banners on this page.
SUMMARY:
| Name | .Locky |
| Type | Ransomware |
| Danger Level | High (Ransomware viruses are of the highest threat level there is) |
| Symptoms | PC slowness followed by file encryption and ransom demand. |
| Distribution Method | Trojan horse “droppers”, sometimes directly via email attachments and malicious websites. |
| Detection Tool | Ransomware are notoriously difficult to track down, since they actively try to deceive you. Use this professional Locky Virus scanner to make sure you find all files related to the infection.Sponsored |
Locky Virus Ransomware Removal
Readers are interested in:
Reboot in Safe Mode (use this guide if you don’t know how to do it).
This is the first preparation.
Keep in mind, SpyHunter’s malware detection tool is free. To remove the infection, you'll need to purchase its full version. More information about SpyHunter and steps to uninstall.
The first thing you must do is Reveal All Hidden Files and Folders.
- Do not skip this. Locky Virus may have hidden some of its files.
Hold the Start Key and R – copy + paste the following and click OK:
notepad %windir%/system32/Drivers/etc/hosts
A
new file will open. If you are hacked, there will be a bunch of other
IPs connected to you at the bottom. Look at the image below:
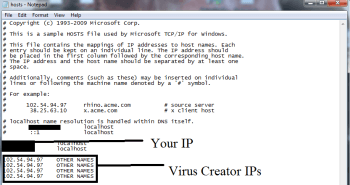
127.0.0.1 188.138.88.184 #Locky – Ransomware
127.0.0.1 85.25.138.187 #Locky – Ransomware
Attention: Some of the new Locky version might be using other IPs.
If there are suspicious IPs below “Localhost” – write to us in the comments.
Type msconfig in the search field and hit enter. A window will pop-up:
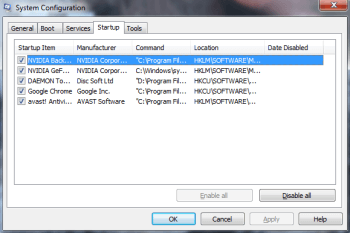
Go in Startup —> Uncheck entries that have “Unknown” as Manufacturer.
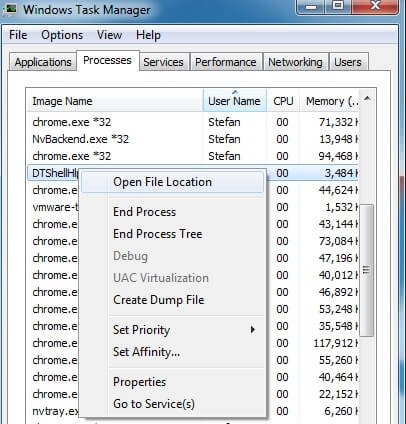
Press CTRL + SHIFT + ESC simultaneously. Go to the Processes Tab. Try to determine which ones are a virus. Google them or ask us in the comments.
WARNING! READ CAREFULLY BEFORE PROCEEDING!
Keep in mind, SpyHunter’s malware detection tool is free. To remove the infection, you'll need to purchase its full version. More information about SpyHunter and steps to uninstall.
Right click on each of the virus processes separately and select Open File Location. End the process after you open the folder, then delete the directories you were sent to.
Type Regedit in the windows search field and press Enter. Once inside, press CTRL and F together and type the virus’s Name.
Search for the ransomware in your registries and delete the entries. Be extremely careful – you can damage your system if you make a big mistake.Type each of the following in the Windows Search Field:
- %AppData%
- %LocalAppData%
- %ProgramData%
- %WinDir%
- %Temp%
Look for these files:
%UserpProfile%\Desktop\_Locky_recover_instructions.bmp%UserpProfile%\Desktop\_Locky_recover_instructions.txt%Temp%\[random].exe
HKCU\Software\Locky
HKCU\Software\Locky\id
HKCU\Software\Locky\pubkey
HKCU\Software\Locky\paytext
HKCU\Software\Locky\completed
HKCU\Control Panel\Desktop\WallpaperHow to Decrypt files infected with the Locky Virus
There is only one known way to remove the virus’ encryption that MAY work (no guarantees) – reversing your files to a previous state. There are two options you have for this:
The first is using a system backup. Search for Backup and Restore in the windows search field —–> “Select another backup to restore files from”
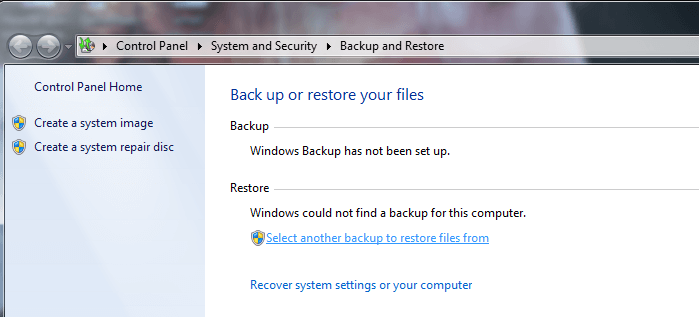
If you have no backups, your option is Recuva
Go to the official site for Recuva and download its free version. When you start the program, select the file types you want to recover. You probably want all files. Next select the location. You probably want Recuva to scan all locations.
Click on the box to enable Deep Scan. The program will now start working and it may take a really long time to finish, so be patient and take a break if necessary.
You will now get a big list of files to pick from. Select all relevant files you need and click Recover.
Subscribe to:
Comments (Atom)

 Best Malware Removal Tools
Best Malware Removal Tools
 Malware Prevention Tips
Malware Prevention Tips
